24/7/365 Monitoring & Rapid Alerts
When you’re a busy MSP managing multiple tenants, you need to know rapidly if anything unusual is going on. The last thing you need is an angry client asking why you didn’t spot cybercriminals were in their M365 accounts. The Microsoft warnings assume that cybercriminals haven’t breached your MSP. How would you know that one of your engineers hasn’t inadvertently given away their username and password? Remember, MFA is still really easy to get around.
BUT, without M365 automation how can you possibly achieve this?
You’d need a whole team of engineers constantly checking everywhere that cybercriminals could hide out or gain entry. Not an easy task, very time consuming, expensive and extremely boring. Also, how would you have time to do anything else?
These are the exact problems we encountered when we ran our MSP. So, we created these Tools to take away our biggest fear: one morning we would wake up to discover all our 150+ tenants had been breached.
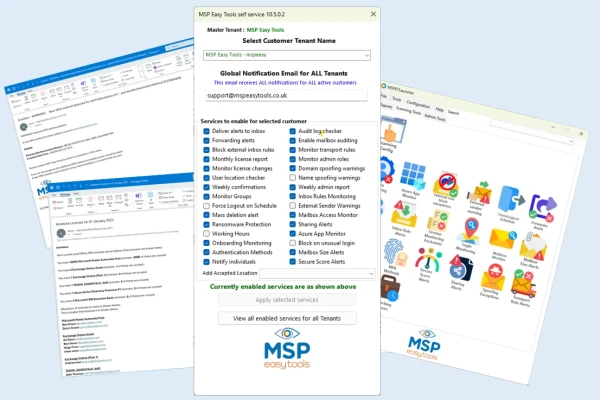
Here's just a few of our Monitoring & Alerting Tools:
More tools added every month based on our worldwide MSP members' votes.
Monitoring & Alerting Tools |
What It Does |
Why |
| Azure/Entra ID Monitoring & Alerting Tools | ||
|
Location |
Monitors and alerts for any suspicious logins outside of your accepted locations. Use the tool to add new accepted locations by IP address, city, region or country and can be scheduled by time if required. Can also choose to instantly block suspicious account activity. |
Most cyber attacks happen from suspicious locations. Monitor exactly what you need, confident that accounts are instantly blocked, if that's what you choose. |
|
Admins |
Monitors and alerts for new admins and changes to admin roles. |
Admin access is the golden ticket for cybercriminals. Never miss when new ones are created/changed. |
|
MFA Authentication Methods |
Monitors and alerts for any new MFA authentication methods. Will be applied to all new accounts in tenant once activated, unless you choose to monitor individually. |
Evil proxy attacks make use of authentication methods by registering a bogus method. Unless you are monitoring for this, you'll never know. |
|
Azure App Monitor |
Detect Azure applications and stop alerts for any that are legit |
Azure apps are a key way cybercriminals can gain access to systems. Lets you keep on top of this risk |
|
Forced Logout On Schedule |
Forces individual user/s or the entire tenant to logout from all devices connected to O365 on a predefined schedule. Revokes the access token to force the user to resupply credentials and MFA. Number of days before each forced logout can be selected and the first day of the forced logout chosen. |
Could be implemented at business downtimes/ major holiday shutdowns. Removes cyber threat |
|
Working Hours |
Control the schedule for working hours. Enable and disable accounts across week and also within global setting |
Security of accounts is massively improved if it can be disabled during inactive periods |
|
License Monitoring Exclusions |
By default system monitors and notifies for all tenants in your partner portal. Also, give option to exclude any tenants you don’t want to monitor. |
Allows you to keep on top of license changes and spot if any have been added that shouldn’t have been . |
|
Groups |
Monitors and alerts on groups when an external user is added. |
Cybercriminals will secretly add themselves to a group, so you need to stay in the know. |
| Exchange / Mailbox Monitoring & Alerting Tools | ||
|
Forwarders |
Allows you to approve/remove external forwarders that were detected by the live system. Can automatically block. |
Quickly spot any forwarders placed on accounts and rapidly approve or remove them, leaving nothing to chance. |
|
Mailbox Monitor |
Choose the mailboxes you want to monitor for delegated permissions. Also approve/remove detected delegates. |
Know rapidly if any permissions are added to key mailboxes and rectify just as quickly. |
|
Mailbox Size Alerts |
Alerts when a mailbox is reaching size capacity before functionality is lost. You can choose the alert threshold. Clearly defines mailbox folders and sizes. |
Avoid customer down-time and stress. Pro-actively perform house keeping on mailboxes before they reach their limits. |
|
Transport Rules |
Spot any rules that may be set to re-direct mail. |
Rapidly detect and fix what could be a cyber threat. |
|
Inbox Rules |
Alerts on all inbox rules that are detected in any scanned mailbox. You can choose which mailboxes you want scanning. |
Again, rapidly detect and fix what could be a cyber threat. |
|
External Sender Warning Exceptions |
Allows warnings to be splashed on emails that are from external senders. Also allows you to select accounts you do not want this applied to |
Be clear on any emails that are from external users. |
|
Internal Spoofing Protection |
Detects spoofed emails and flags a warning banner. |
Make sure that you know if messages are spoofed – at a glance. Keeps your business safer. |
|
Add Exception For Inbox Rules |
If you have enabled inbox rule blocker, use when you need legitimate rules to function. |
Make sure risky inbox rules aren’t posing a threat. Only let the ones through that you know are 100% legit. |
| Sharepoint / OneDrive Monitoring & Alerting | ||
|
Sharing Alerts |
Get alerted to any external sharing operations. |
You need to know when external sharing of files is happening to keep your reputation and customers safe. |
|
Mass Deletion Alert |
Be aware if any mass deletions/changes or moves are made in SharePoint data. Customisable to data size alert levels. |
Make sure you know rapidly if any SharePoint data is moved, renamed (which could be done with Ransomware attacks) and deleted in large quantities. |